Single sign-on (SSO) is an authentication method through which users can log in to multiple services by being authenticated only in one of the services. This free business from the need to hold passwords in their databases, login troubleshooting, and decreases the damage a hack can cause.

One of the most common examples of SSO is Google apps. By signing in to the Google accounts, you can access any services of Google, like Gmail, Drive, Slides, Docs, etc.
Many technologies are used to provide a Single Sign-On feature. The two most commonly used techniques for providing SSO functionality are OAuth and SAML. Both of these technologies authenticate a user and provide him access to other services and applications. But the working of Both the technology is different.

When we talk about Single Sign-On (SSO), many technologies come to our mind. A few are listed below:
In this blog, we will be learning about the SAML workflow. As each of the above terms is a big topic in itself.
SAML stands for Security Assertion Markup Language. It is an XML-based open-standard that allows identity providers (IdP) to pass authorization credentials to service providers (SP). It means that you can use one set of credentials to log in to many different services or applications. SAML use Extensible Markup Language (XML) for standardized communications between the identity provider and service providers.
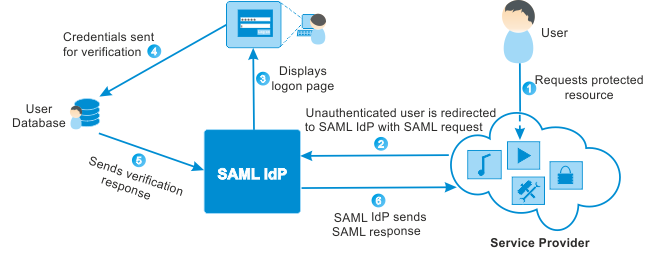
Now, you must be thinking about what IdP and SP are. So, SAML has two types of providers — Identity Provider and Service Provider. Let’s learn more about these two.
Identity Provider — An identity provider is an application that performs authentication and verifies the user using the login credentials. The identity provider sends a SAML Assertion that is an XML document to the service provider that contains the user authorization.
Service Provider — After successful authentication from IdP, the user redirects to the service or application he or she wants access to. This service or application is known as Service Provider (SP).
A SAML IdP generates a SAML response in an XML document based on the configuration that is mutually agreed to by the IdP and the SP. After receiving the SAML assertion, the SP validates the assertion by checking if it is coming from a valid IdP and then fetch the required information from the assertion: the username, attributes, and so on.
To do the above process, the SP requires the following: